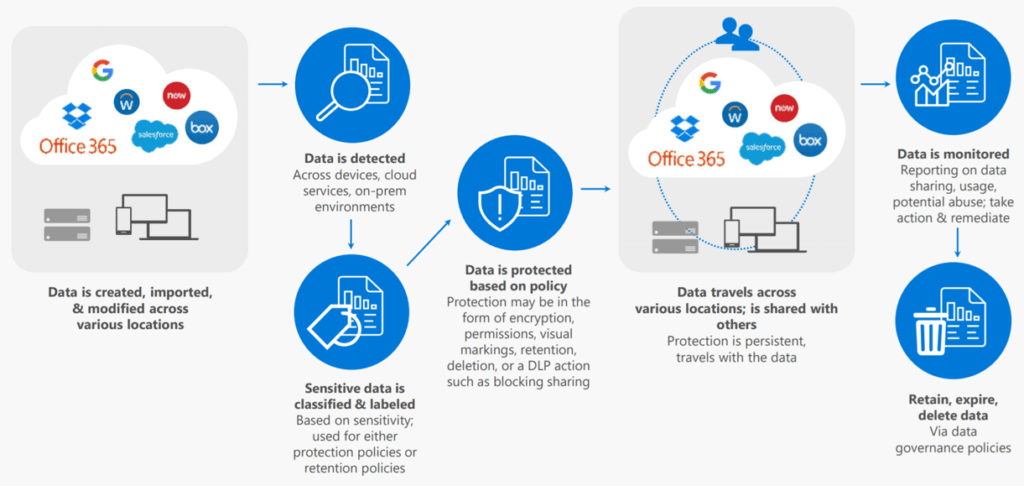
All Microsoft 365 subscriptions come with Exchange Online Protection, which includes defenses against spam, viruses, and phishing that are enabled by default. For additional protection, you can configure optional policies available in all subscription types, and you can enable Defender for Office 365, a feature…